In /r/3778 we added support for a new authenticode signing type in Makefile.mingw named CUSTOM_AUTHENTICODE which should contain the path to a script/batch file/whatever to do the code signing. The Makefile.mingw will pass the file to be signed as the first parameter and the description string as the second parameter.
This was required because I now have to use a Hardware Security Module (HSM) to sign the releases and the only way I’ve been able to get it to work is via signtool from the Windows SDK. For whatever reason, signtool seems to only work under command prompt and I could not find any way to make it work under msys2.
After a lot of trial and error I realized that if I had the Makefile.mingw call the batch file directly without using cmd.exe that it would just work. So here’s the break down.
In my local.mak I have the following line:
CUSTOM_AUTHENTICODE=/home/grim/sign.bat
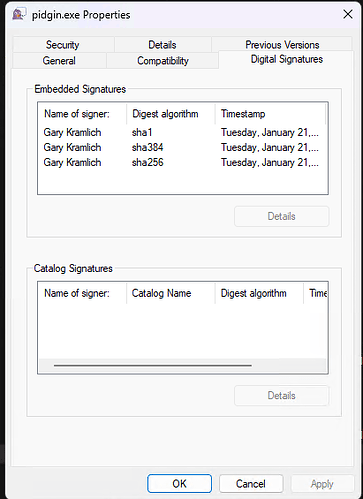
In /home/grim/sign.bat I run signtool three times. This is done to create a file digest with SHA-1, SHA-256, and SHA-384 algorithms. Old versions of Windows don’t support SHA-384 but they should still work with SHA-1 and SHA-256. The /as after the /fd argument is what allows us to append another signature into the binary.
"c:\Program Files (x86)\Windows Kits\10\bin\10.0.26100.0\x64\signtool.exe" sign /n "Gary Kramlich" /i "Sectigo Public Code Signing CA R36" /sha1 FB9BD32A13C173BACFF9581397D4488B5B0CD63E /d %2 /fd sha1 /du "https://pidgin.im" /tr "http://timestamp.comodoca.com/rfc3161" /td certHash %1
"c:\Program Files (x86)\Windows Kits\10\bin\10.0.26100.0\x64\signtool.exe" sign /n "Gary Kramlich" /i "Sectigo Public Code Signing CA R36" /sha1 FB9BD32A13C173BACFF9581397D4488B5B0CD63E /d %2 /fd sha256 /as /du "https://pidgin.im" /tr "http://timestamp.comodoca.com/rfc3161" /td certHash %1
"c:\Program Files (x86)\Windows Kits\10\bin\10.0.26100.0\x64\signtool.exe" sign /n "Gary Kramlich" /i "Sectigo Public Code Signing CA R36" /sha1 FB9BD32A13C173BACFF9581397D4488B5B0CD63E /d %2 /fd sha384 /as /du "https://pidgin.im" /tr "http://timestamp.comodoca.com/rfc3161" /td certHash %1
These commands can probably be simplified to not use three arguments to select the proper certificate, but it’s working for now and I didn’t want to tinker with it anymore as I’ve spent many hours today working on this.
And with all that we can sign again!